Cloud security is becoming a key component of digital transformation strategies as businesses are migrating their infrastructures and operations to cloud-based platforms. The traditional cloud security architecture has grown beyond traditional boundaries as hybrid work, cloud application security with AI adoption, and multi-cloud setups become the norm. However, with this growth comes evolving cyber threats.
In this blog, we will explore the most recent advances in cloud computing security, highlighting current trends, key solutions, and best practices. Let’s get started with WeCloudData!
What is Cloud Security?
The term “cloud security” describes a broad range of technologies, tools, regulations, and industry best practices designed to protect cloud computing-related infrastructure, apps, and data. It ensures that cloud-based systems remain secure, compliant, and resilient against both internal and external threats.
Fundamentally, cloud security is about protecting:
- Confidentiality: Ensuring that only authorized users can access sensitive data.
- Integrity: Protecting data from unauthorized modification.
- Availability: Ensuring systems and data remain accessible to authorized users when needed.
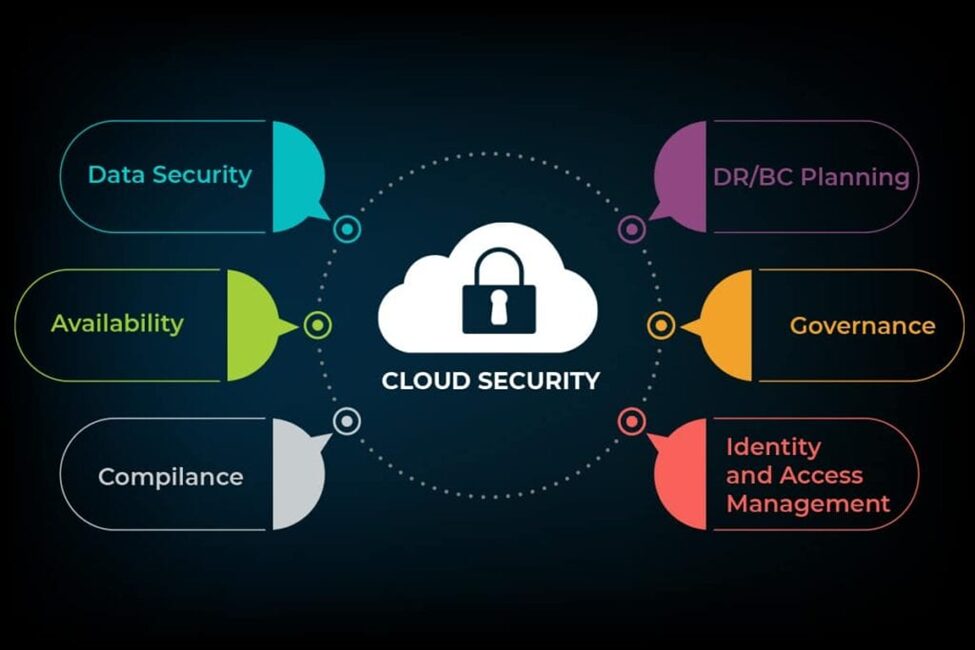
Why Cloud Security Matters More Than Ever
Cloud computing is no longer a luxury, it’s the foundation of innovation. Data, apps, and services are available from any location in today’s hyperconnected world, which increases the risk to cloud computing security. The cyber threat dynamic now includes more advanced distributed denial of service (DDoS) attacks, insider threats, and zero-day vulnerabilities.
The 2024 Cost of a Data Breach Report discovered that 40% of all data breaches involved data distributed across multiple environments. This means that the best-laid plans often fail in the cloud environment, and organizations must prioritize a defense-in-depth strategy. The Cloud Security Alliance (CSA) promotes a proactive security approach that includes user education, data protection, risk management, and compliance.
Key Elements of Modern Cloud Security
Cloud security is no longer limited to firewalls or encryption; it’s more complicated and complex, containing a broad spectrum of capabilities. Core capabilities include:
Cloud Security Posture Management (CSPM): Real-time cloud misconfiguration detection and correction using automated technologies.
Cloud Access Security Broker (CASB): The Cloud Access Security Broker (CASB) enforces identity verification and DLP policies to guarantee safe access between users and cloud services.
Zero Trust Architecture: Zero Trust Architecture reduces lateral movement within the network by implementing least privilege access and continuous authentication.
Cloud Web Security: Prevents malicious content and phishing attempts at the browser level using cloud-delivered security layers.
Organizations must integrate these components while also aligning with regulatory frameworks such as GDPR and ISO/IEC 27017.
Cloud Security- A Shared Responsibility
Cloud computing security is the shared responsibility between the client/organization and the cloud service provider, like Microsoft Azure, AWS, and Google Cloud Platform (GCP). These companies, cloud service providers, provide a robust baseline security, but the share of responsibility differs based on the service model:
- PaaS: Providers secure the platform; clients secure usage and data.
- SaaS: Providers handle most layers; clients manage user access and configurations.
- IaaS: Customers manage OS, data, and applications.
Major vulnerabilities can result from a gap in understanding these roles, especially when cloud data scientists and engineers deploy ML models, pipelines, and sensitive analytics environments on the cloud more frequently.
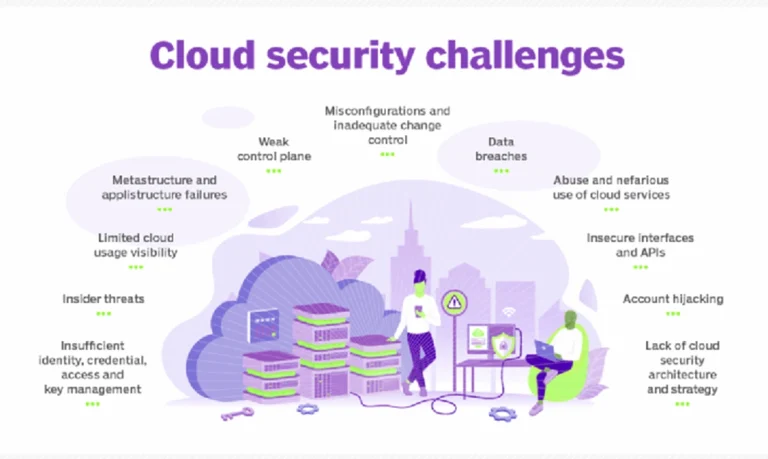
Cloud Security Challenges in 2025
Major cloud security challenges are;
Visibility and Control
With so many cloud services accessible through third parties and outside of corporate networks, it’s simple to lose track of who is accessing your data and how.
Compliance Complexity
Enterprises implementing public or hybrid cloud deployments frequently need help with regulatory compliance management. Organizations are solely responsible for their data privacy and security. High dependency on third-party management solutions might result in expensive compliance problems.
API Exploits
Weakly protected APIs have become entry points for attackers, necessitating strong authentication and a logging mechanism.
Misconfigurations
Incorrect permissions and access policies are among the top causes of breaches, particularly in dynamic, DevOps-driven cloud environments.
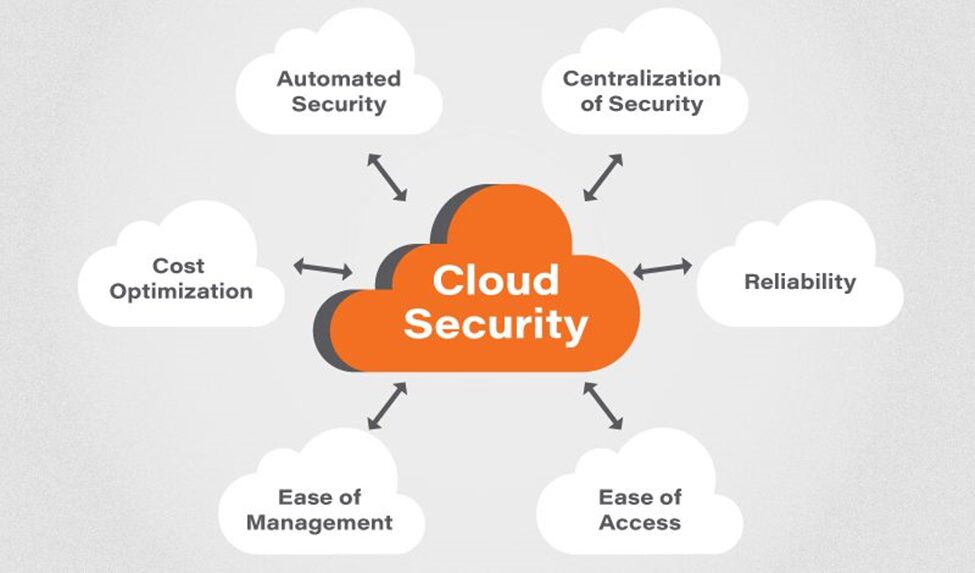
Cloud Security Benefits and Trends
The rise of cloud security solutions and SECaaS (Security-as-a-Service) has significantly boosted organizational resilience. Modern cloud security tools and technologies offer:
- Automation: Continuous threat monitoring, remediation, and anomaly detection.
- Scalability: Security frameworks that grow with the organization’s cloud infrastructure.
- Centralized Control: Unified dashboards for governance, cloud web security, and compliance.
- Reduced TCO: Organizations benefit from lower infrastructure and staffing costs when using managed security services.
In today’s fast-paced digital economy, cloud computing security is your first line of defense and your competitive advantage. Whether you’re running customer-facing apps or internal AI models, ensuring robust cloud application security solutions is essential for protecting your business and your data.
Learn Cloud Computing With WeCloudData!
Want to become a cloud data scientist, cloud engineer, or security architect? At WeCloudData, we help professionals like you break into the tech industry with career-focused Cloud Computing & Data Programs designed by industry experts in Canada.
Our top rated Cloud Engineer Track delivers a comprehensive, hands-on approach to cloud engineering, equipping you with the skills to design, deploy, and manage secure, scalable, multi-cloud environments. It familiarizes you with the Cloud Security Architecture and more to become a confident cloud security engineer. The courses included in the cloud computing learning track for becoming a cloud security engineer include;
- Python Fundamentals
- Introduction to Linux
- Introduction to Docker
- AWS Fundamentals
- Azure Fundamentals
- GCP Fundamentals
Why This Program?
- End-to-End Cloud Mastery: From core principles to advanced architectures across AWS, Azure, and GCP.
- Enterprise-Grade Skills: Learn industry best practices for DevOps, resilience, and cost-optimized solutions.
- Real-World Readiness: Apply knowledge through hands-on projects and case studies mirroring modern IT challenges with Cloud Security Architecture
Who Should Enroll?
- Aspiring Cloud Engineers and Architects
- DevOps & SRE Professionals expanding their cloud expertise
- Tech professionals transitioning to multi-cloud environments
Visit WeCloudData to start your journey into Cloud Computing!

